Cover your Ass
Pwnagotchi
Pwnagotchi
Couldn't load pickup availability
Includes:
Raspberry Pi 02W, 32 GB SD Card, Waveshare 2.13" E-Ink Display., NO PI SUGAR or OTHER MODULES.
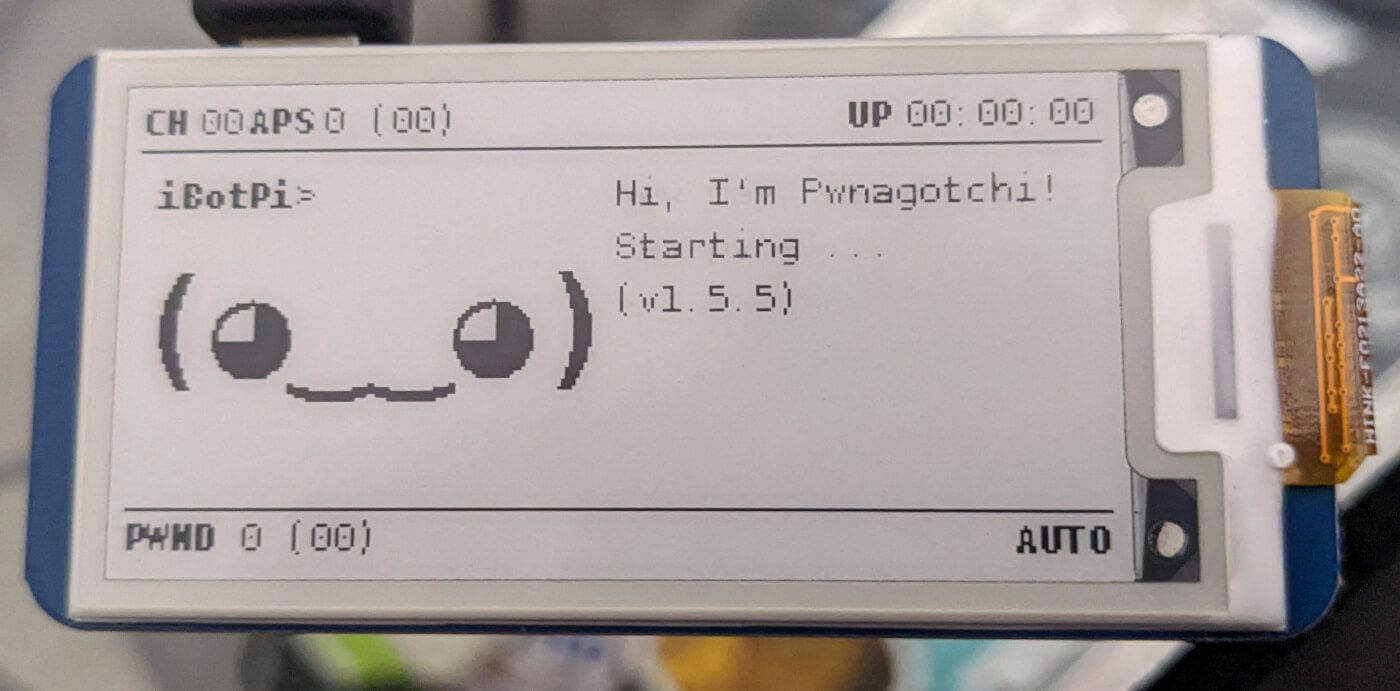
The Faces of the Pwnagotchi Explained:
(⇀‿‿↼) sleeping
This is the state the unit will start from. Moreover, from time to time your Pwnagotchi will also perform naps of a few seconds while hopping among WiFi channels.
(≖‿‿≖) awakening
The unit is in the last seconds of its nap.
(◕‿‿◕) awake / normal
This face is the neutral awake status of the unit. It’ll be used to smooth the transition between other moods and in general when there’s no external cause of either positive or negative moods. It can also be used, randomly, when another unit is encountered for the first time (each unit keeps a record of all the units it met).
( ⚆⚆), (☉☉ ) observing (neutral mood)
Your Pwnagotchi is waiting and observing what bettercap can find on all the channels it’s hopping on.
( ◕‿◕), (◕‿◕ ) observing (happy)
When there’s one or multiple units nearby and their cumulative bond counter is greater or equal than the personality.bond_encounters_factor, this will be the unit’s face while observing.
(°▃▃°) intense
The unit is sending an association frame to an access point in order to force it to leak the PMKID.
(⌐■_■) cool
The unit is deauthenticating a client station from an access point. This face can also be picked randomly when meeting another unit for the first time.
(•‿‿•) happy
Your Pwnagotchi is happy in one of the following cases:
- The AI just finished loading and it’s ready.
- Valid key material for an access point has just been captured.
- In MANU mode, if the last session was short or if any handshake has been captured during it.
- When another unit is met and the bond level is high enough.
(^‿‿^) grateful
Your Pwnagotchi is grateful in one of the following cases:
- The cumulative bond level of nearby units is at least five times the
personality.bond_encounters_factor. - The unit should be bored, but there are enough friendly units nearby.
- The unit should be sad, but there are enough friendly units nearby.
- The unit should be lonely, but there are enough friendly units nearby.
(ᵔ◡◡ᵔ) excited
Your Pwnagotchi is excited in one of the following cases:
- The number of epochs with some activity is greater or equal than
personality.excited_num_epochs. - Randomly if a unit with a high bond level is met.
- If you have unread PwnMAIL messages on that unit.
(✜‿‿✜) smart
Randomly if a unit with a med-high bond level is met.
(♥‿‿♥) friendly
Randomly if a unit with a high bond level is met.
(☼‿‿☼) motivated
Your Pwnagotchi just scored the best reward level in its existence or just met a unit with a high bond.
(≖__≖) demotivated
Your Pwnagotchi just scored the worst reward level in its existence.
(-__-) bored
If there are no friendly units around and the amount of consecutive inactive epochs reached personality.bored_num_epochs.
(╥☁╥ ) sad
If there are no friendly units around and the amount of consecutive inactive epochs reached personality.sad_num_epochs.
(ب__ب) lonely
If your Pwnagotchi just lost contact with a friendly unit that was nearby, or if the amount of missed interactions with access points or client stations (the amount of times it tried to send some type of packet but missed the target because it isn’t in range anymore) is greater or equal than personality.max_misses_for_recon. And there are no friendly units around.
(☓‿‿☓) broken
Your unit is rebooting either as a coping strategy for the blindness bug, or after installing an update.
(#__#) debugging
Used for debug and test messages on screen.
WiFi Handshakes 101
In order to understand why it’s valuable to have an AI that wants to eat handshakes, it’s helpful to understand a little bit about how handshakes are used in the WPA/WPA2 wireless protocol.
Before a client device that’s connecting to a wireless access point—say, for instance, your phone connecting to your home WiFi network—is able to securely transmit to and receive data from that access point, a process called the 4-Way Handshake needs to happen in order for the WPA encryption keys to be generated. This process consists of the exchange of four packets (hence the “4” in “4-Way”) between the client device and the AP; these are used to derive session keys from the access point’s WiFi password. Once the packets have been successfully exchanged and the keys are generated, the client device is authenticated and can start sending and receiving data packets (now secured by encryption) to and from the wireless AP.
So…what’s the catch? Well, these four packets can easily be “sniffed” by an attacker monitoring nearby (say, with a Pwnagotchi 😇). And once recorded, that attacker can use dictionary and/or bruteforce attacks to crack the handshakes and recover the original WiFi key. In fact, successful recovery of the WiFi key doesn’t necessarily even need all four packets! A half-handshake (containing only two of the four packets) can be cracked, too—and in some (most) cases, just a single packet is enough, even without clients.
In order to eat collect as many of these crackable handshake packets as possible, Pwnagotchi uses two strategies:
- Deauthenticating the client stations it detects. A deauthenticated device must reauthenticate to its access point by re-performing the 4-Way Handshake with the AP, thereby giving Pwnagotchi another chance to sniff the handshake packets and collect more crackable material.
-
Sending association frames directly to the access points themselves to try to force them to leak the PMKID.
TIPS:
In addition to the two above methods, there is a third method by which Pwnagotchi completely passively collects handshakes: if a device happens to be attempting to authenticate to an AP on the same channel that the unit just so happens to be monitoring at that time, Pwnagotchi may eat collect handshakes completely by chance (and not as the result of a deauthentication or PMKID attack).
For instance, even if you whitelist your home network so that Pwnagotchi knows to never actively attack it, you will still passively collect handshakes for that network by chance as your Pwnagotchi is simply sniffing packets in its environment. (If you’re monitoring a residential area, you might see an uptick in handshakes passively acquired as your neighbors turn on their devices in the morning and again in the early evening when they return home after work.)
All the handshakes captured by your Pwnagotchi are saved into .pcap files on its filesystem. Each PCAP file that Pwnagotchi generates is organized according to access point; one PCAP will contain all the handshakes that Pwnagotchi has ever captured for that particular AP. These handshakes can later be cracked with proper hardware and software.
(Information above provided by www.pwnagotchi.ai, Photos, Videos, and other forms of multimedia Information obtained from 3rd party sources)
*LEGAL DISCLAIMER*
ALL DEVICES SUCH AS PWNAGOTCHIS ARE CONSIDERABLY ONLY TO BE USED ON ONES OWN DEVICES, NETWORKS, AND FIRMWARES. CHOOSING TO USE ANY SUCH DEVICES ON ANY OTHER NETWORK, PROPERTY, OR 3RD PARTY FIRMWARE WITH A PWNGOTCHI ARE IN FACT ILLEGAL AND, CYA DOES NOT ENDORSE, ENCOURAGE, OR SUGGEST SUCH ILLEGAL ACTIONS NOR DOES IT DO BUSINESS WITH ANYONE WHO DOES. DOING SO IS BY THE BUYERS OWN CHOICE AND THEREFORE WE ARE NOT LEGALLY RESPONSIBLE FOR WHAT THE BUYER CHOOSES TO USE THE NETWORKING/PENTESTING DEVICE FOR. BY PURCHASING THIS DEVICE, YOU ARE AGREEING TO NOT USE IT FOR ANY UNETHICAL OR ILLEGAL ACTIONS.
CYA
Share